Why would you use WordPress security plugins? What a silly question right? Because the obvious answer is that you want to have a secure WordPress site while making hacker’s job harder.
The reason I started with that question is because “regardless of which security plugin you choose to use” relying on plugins alone can never be adequate enough for securing your WordPress built site.
Knowing this, we can now take a look at three of the most popular free WordPress Security Plugins on the market in today’s internet security world giving you better protection against hacking attempts.
- All In One WordPress Security Plugin
- IThemes Security Plugin for WordPress (formerly Better WP Security)
- WordFence Security Plugin
I used all of them amongst others, and found that all of them offer very similar protection such as scans and live traffic monitoring. Personal choice of mine is WordFence (Free version) as I believe it is much easier to use (usually the default setting are good enough, however, you can tweak it according to your WP setup).
WordFence Settings I Use (Download Screenshots here)
The above .zip file highlights the settings that you too can tweak according to your own WordPress setup, but I provided these samples for you because that’s what I use on www.rankya.com SEO blog.
WordPress Security Power Tips Course by RankYa
Additional Precautionary Security Measures: Hide Sensitive Files from General Public.
Unknown to many, your WP installation creates redundant files as well as log files depending on your setup. For example: upon WordPress installation, WP creates a new wp-config.php file. So you can safely delete wp-config-sample.php because its just used for installation.
Also, if your site is built on Apache, then locate your .htaccess file and insert these directives for hiding sensitive file types from general public:
<FilesMatch "(^#.*#|\.(error_log|log|wp-config\.php|php\.ini|\.[hH][tT][aApP].*|bak|config|dist|fla|inc|ini|log|sh|sql|sw[op])|~)$">
Order allow,deny
Deny from all
Satisfy All
</FilesMatch>
Or you can even go further and block certain queries hackers usually use to find vulnerable WordPress sites. (Sample only, use with caution and make sure you backup .htaccess file first)
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteCond %{REQUEST_URI} "!(^|/)\.well-known/([^./]+./?)+$" [NC]
RewriteCond %{SCRIPT_FILENAME} -d [OR]
RewriteCond %{SCRIPT_FILENAME} -f
RewriteRule "(^|/)\." - [F]
RewriteRule ^wp-admin/includes/ - [F,L]
RewriteRule !^wp-includes/ - [S=3]
RewriteRule ^wp-includes/js/tinymce/langs/.+\.php - [F,L]
RewriteRule ^wp-includes/theme-compat/ - [F,L]
RewriteCond %{SCRIPT_FILENAME} !^(.*)wp-includes/ms-files.php
RewriteRule ^wp-includes/[^/]+\.php$ - [F,L]
RewriteCond %{QUERY_STRING} base64_encode[^(]*\([^)]*\) [OR]
RewriteCond %{QUERY_STRING} (<|%3C)([^s]*s)+cript.*(>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2})
RewriteCond %{QUERY_STRING} (;|'|"|%22).*(union|select|insert|drop|update|md5|benchmark|or|and|if) [NC,OR]
RewriteCond %{QUERY_STRING} (localhost|mosconfig) [NC,OR]
#RankYa NOV 2021 added xmlrpc.php
RewriteCond %{QUERY_STRING} (xmlrpc.php|boot.ini|echo.*kae|etc/passwd) [NC,OR]
RewriteCond %{QUERY_STRING} (javascript:).*(;) [NC,OR]
RewriteRule .* index.php [F]
</IfModule>
Additional Precautionary Security Measures: Debug Your WordPress Site Properly
Most often, website owners believe that they can’t debug or they just don’t understand how to find issues regarding their websites.
But debugging your setup not only will reveal issues for fixing and improving the functioning of your site, it can also reveal security holes that hackers usually rely on to breach security of your site. Here’s a solution by RankYa.
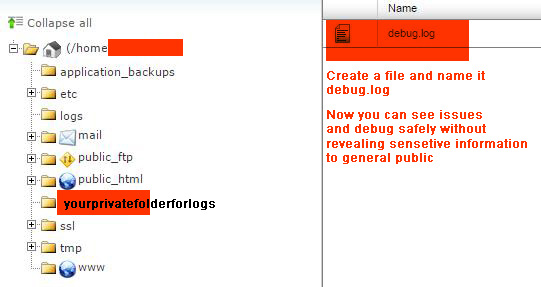
Create a folder that’s above public_html and name it anything you want. Then modify the path in the code below to match the name of that folder (so its not accessible for public to view your debug logs (smart security procedure)). Then create a text file and name it debug.log
Place this code inside wp-config.php file
define( 'WP_DEBUG', true );
define( 'WP_DEBUG_DISPLAY', false );
if ( WP_DEBUG ) {
$pathtodebuglog = dirname(ABSPATH) . '/yourprivatefolderforlogs';
ini_set('log_errors', 1);
ini_set('display_errors', 0 );
ini_set('error_log', $pathtodebuglog . '/debug.log');
}
Now you can conduct regular security audits and see what issues your WordPress site maybe having (particularly with outdated PHP code most plugins are using).
As I’ve said throughout my blog, the weakest point for most WordPress sites are the plugins and themes that are created by individuals who do not thoroughly understand coding, and thus they use coding techniques without sanitizing and without PHP security considerations in their Theme and Plugin code.
These are the biggest security holes for any type of Web Application and Content Management Systems like WordPress. To read more about this important subject, visit my recent post on how to secure and protect your WordPress site from hacker because implementing these measures has served me well to date and my WordPress site hasn’t been hacked before. However, one can’t rest on his laurels, meaning you have to conduct security audits regularly on your web site to stay on the safe side.


